Glory Tips About How To Handle Sql Injection

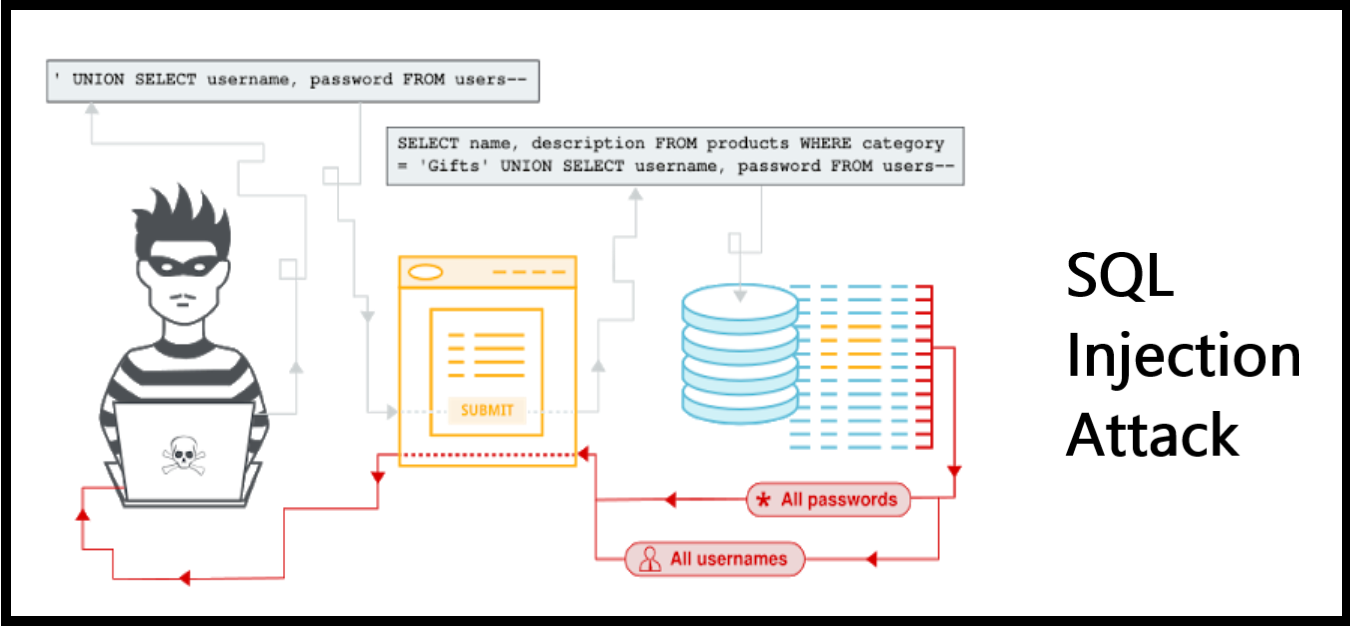
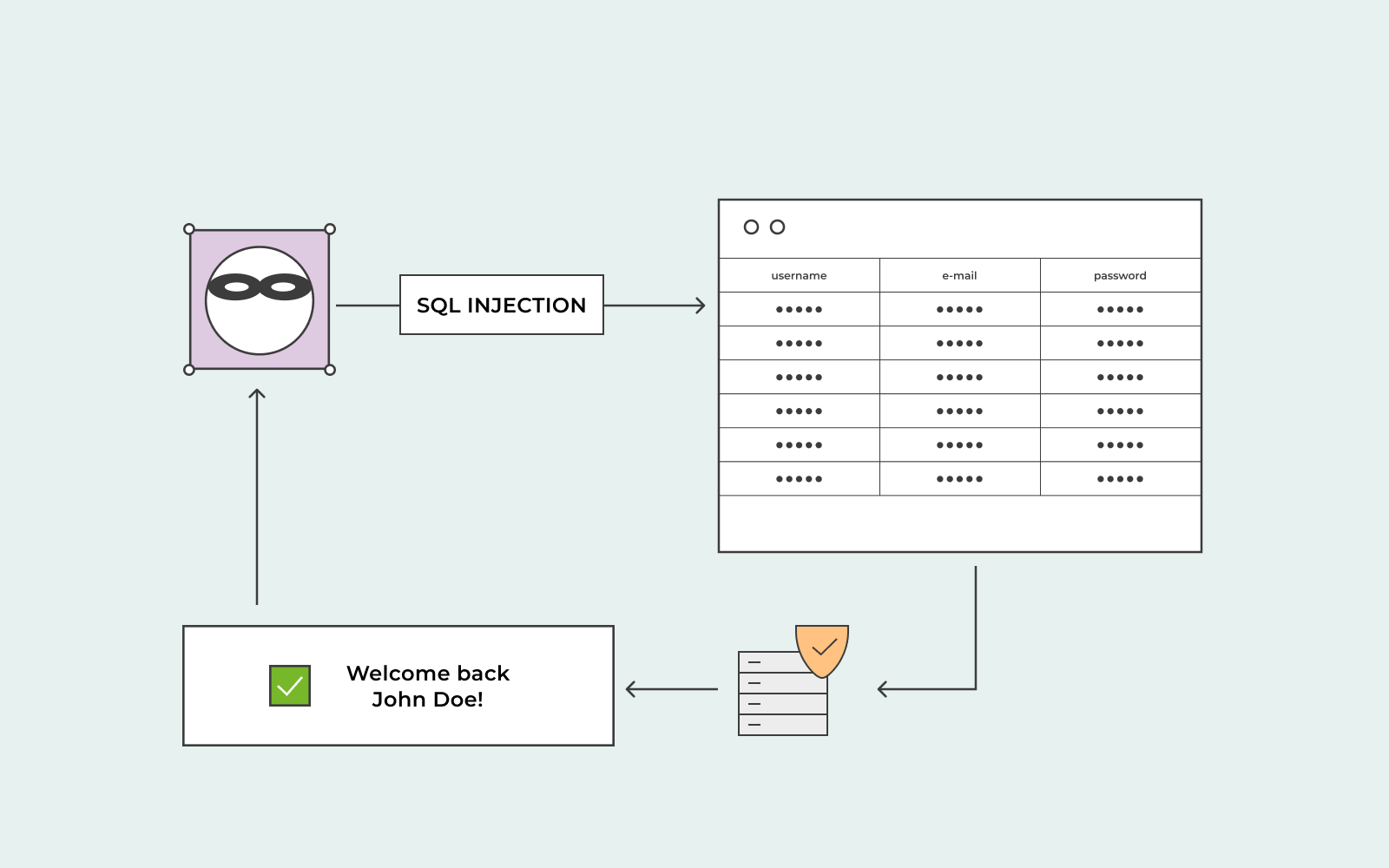
Sql injection is a technique where hackers inject malicious sql queries into a web application's backend database.
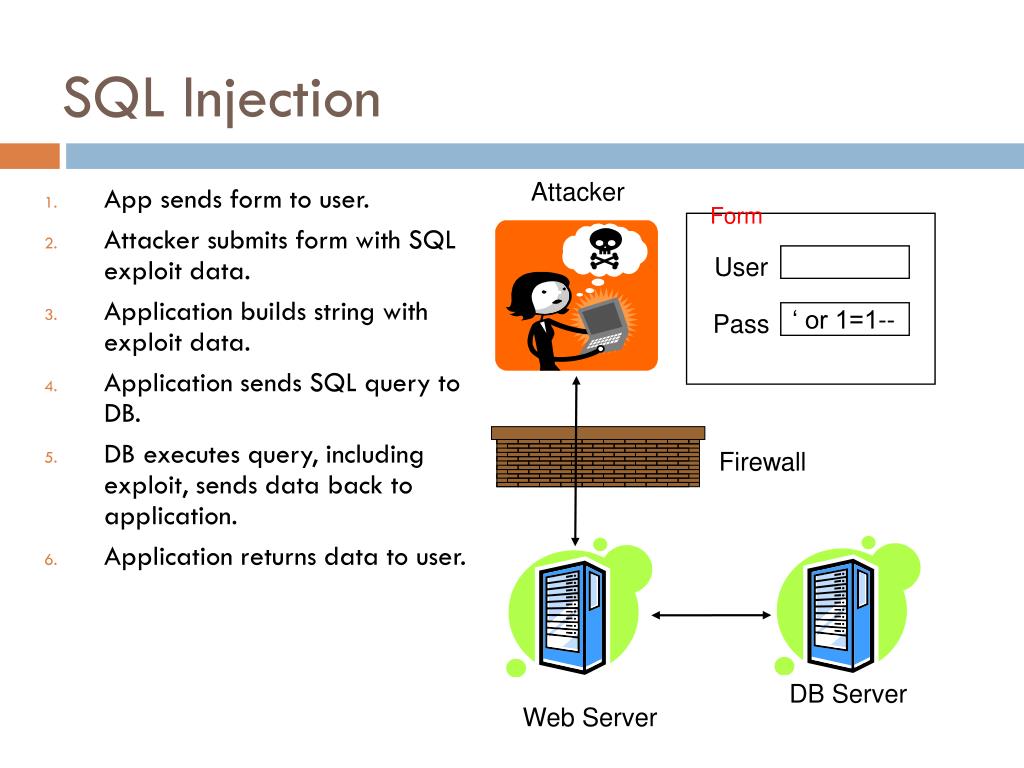
How to handle sql injection. Sql injection vulnerability in the ordergoodsdelivery() function in niushop b2b2c v5 allows attackers to run arbitrary sql commands via the order_id parameter. A successful sql injection exploit can read sensitive data from the database, modify database data (insert/update/delete), execute administration operations on the database. There are different ways in which sql injection can be executed via the above query.
In this blog post, we detailed a sql injection vulnerability within the ultimate member plugin affecting versions 2.1.3 to 2.8.2. It will define what sql injection is, explain where those flaws occur, and provide four. Select your ecosystem c# go java javascript php python sql injection:
This vulnerability arises when the application. The userid is the primary column of the. The five key methods to prevent sql injection attacks include:
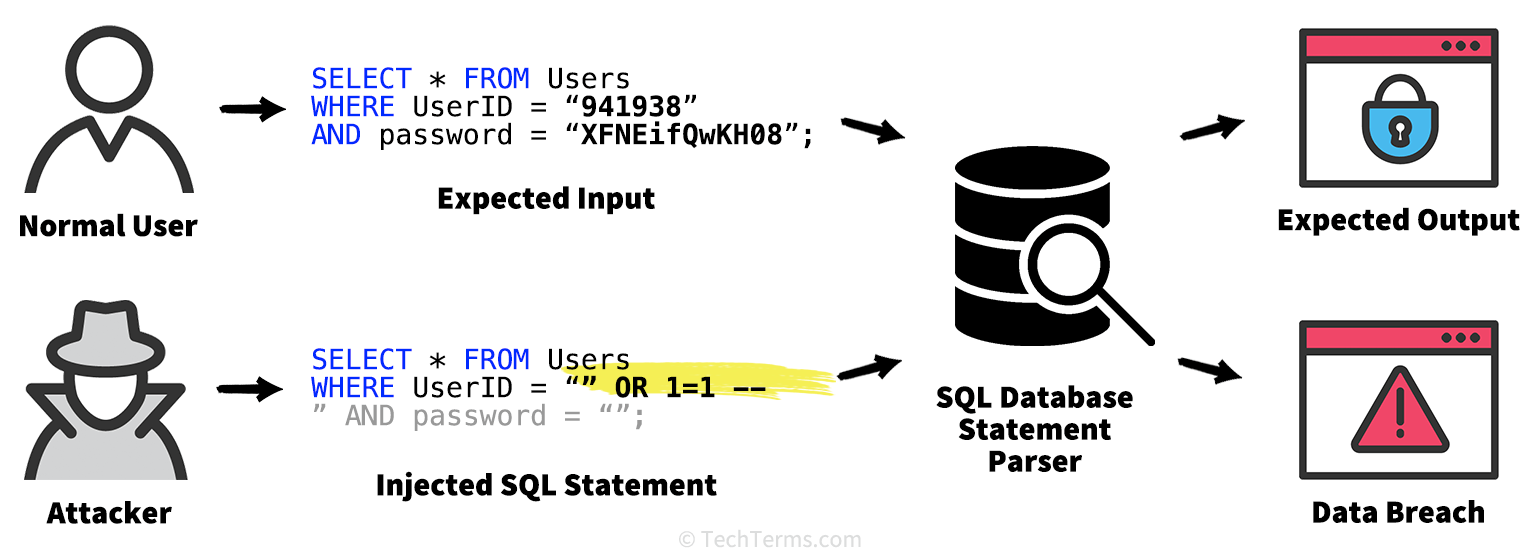
Sql injection is a technique where sql commands are executed from the form input fields or url query parameters. We will discuss two of the simplest and most commonly used ways below. Most sql injection vulnerabilities occur within the where clause of a select query.
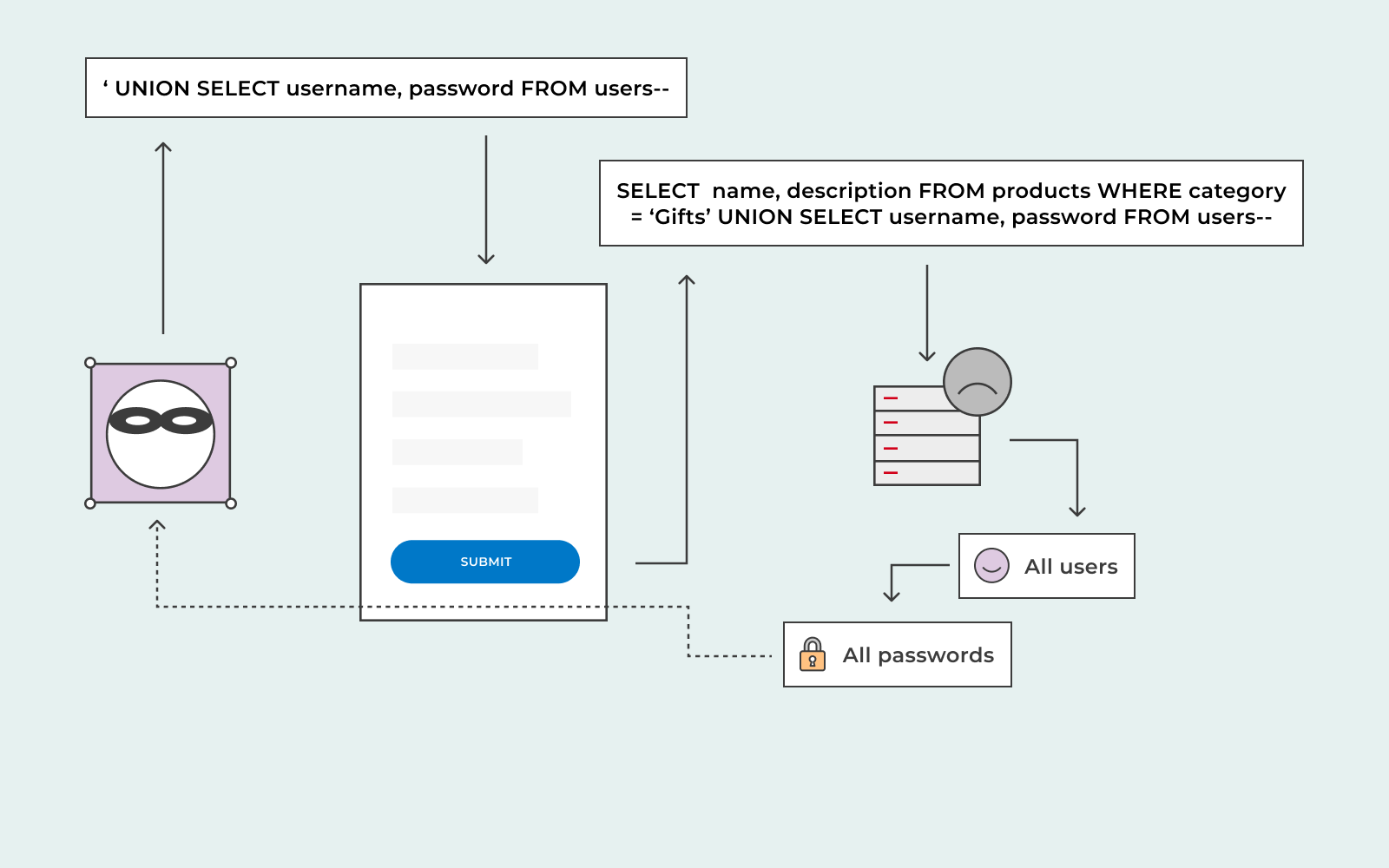
Sql injection in different parts of the query. Some sql injection attacks are designed to remain undetected for a long. Introduction this cheat sheet will help you prevent sql injection flaws in your applications.
With a method signature static iqueryable orderby (this iqueryable source, string.</p> Sql injection (sqli) is the most common web application security attack using code injection technique. The first and simplest approach for sql injection is the approach to end the current string and statement by starting your value with a single or double quote followed.
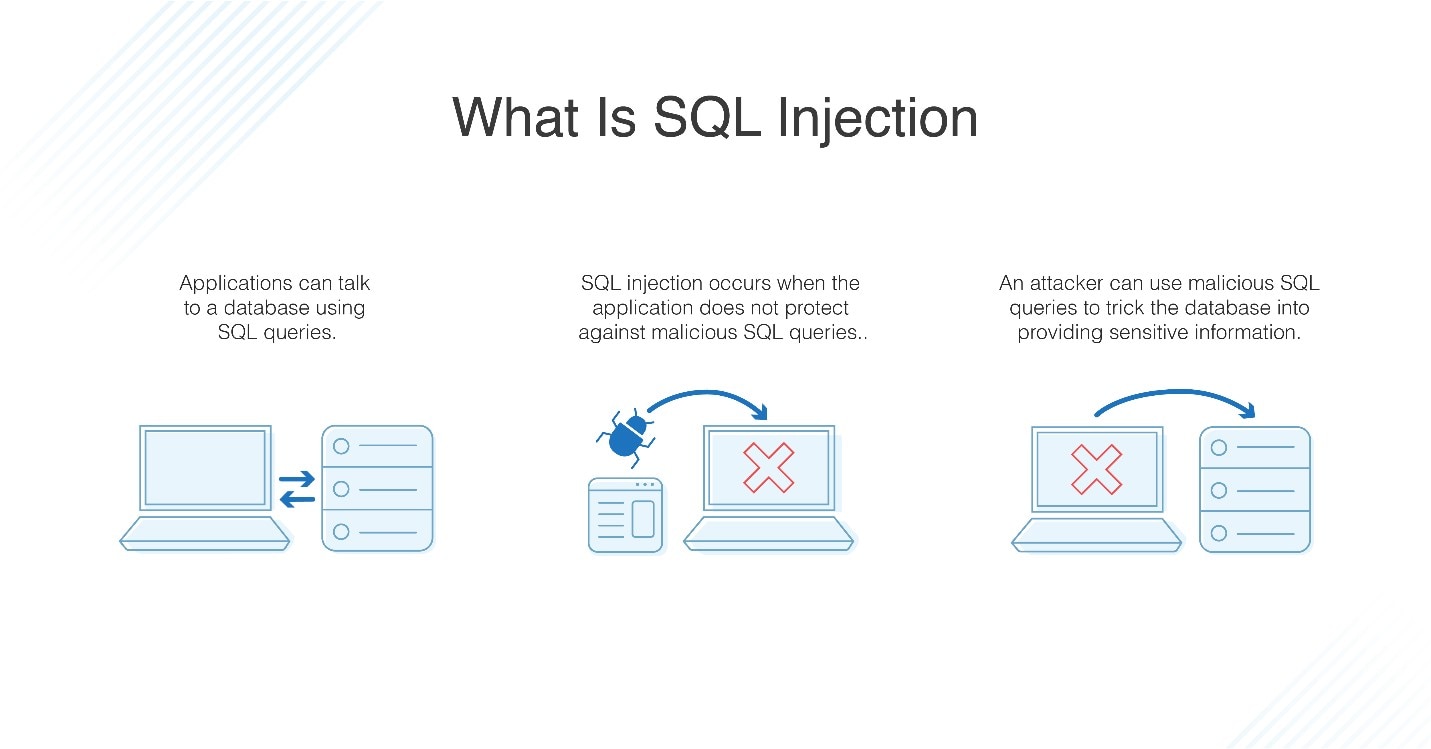
This leads to unauthorized access to the database (a type of. Most experienced testers are familiar with this. Sql injection is a code injection technique that hackers can use to insert malicious sql statements into input fields for execution by the underlying sql database.
Sql injection (or sqli) is one of the most widespread code. Successful attacks allow an attacker to access sensitive data. Sql injection is when you insert or inject a sql query via input data from the client to the application.
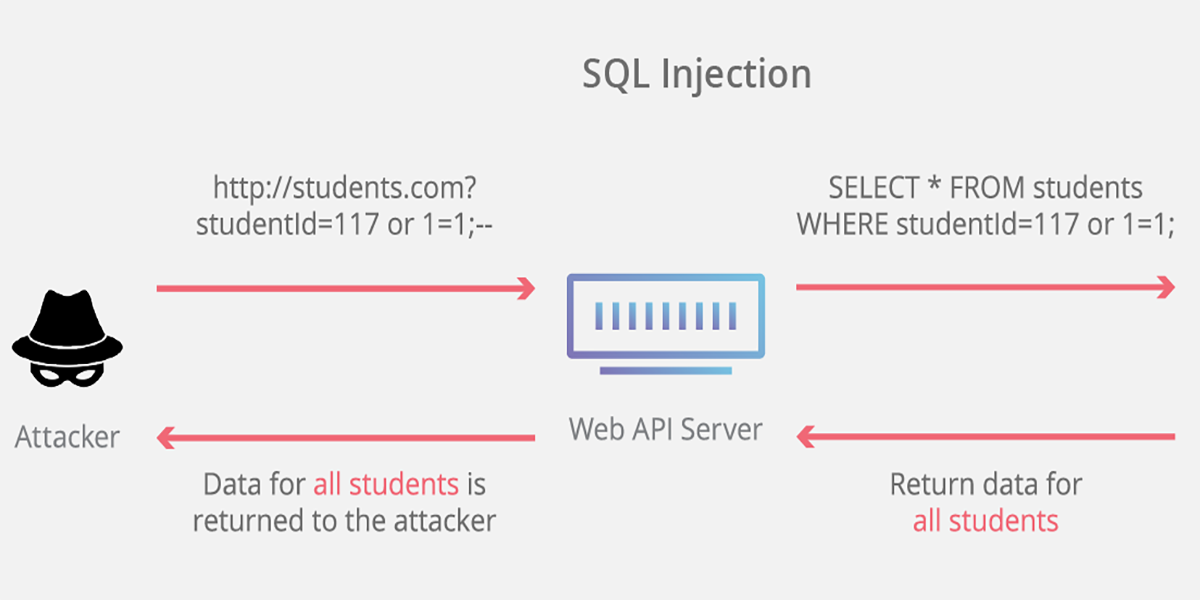
Sql injection (sqli) is a cyberattack that injects malicious sql code into an application, allowing the attacker to view or modify a database. Sql injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an sql statement that you will unknowingly run. The basics what is sql injection?
Did you know hackers steal billions of dollars every year? How does sql injection works? Suppose we have a database table named tbluser which stores data of application users.